Hack Wifi In Kali linux
Let’s begin!
So, to begin with the hack first I had to search for different WiFi signals in the nearby area, there were a few of them.

BUY HACKER T-SHIRT
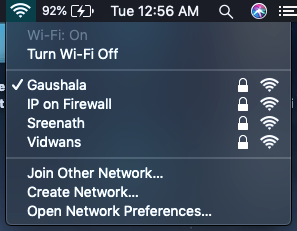
Once, I checked for the WiFi networks then I turned on my Kali machine to hack into one of these networks. I opened up my terminal and typed in
wifite
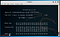
Wifite, is one of the most user friendly tool out there you can use for hacking WiFi ( that’s just my opinion ). The information shown below popped up.

Now if you are a hacker, then you already know which network I would have tried to hack in. Yes, “IP on Firewall”. I mean if you name your WiFi, Firewall then it is like asking nearby hackers to mess with you, and so I choose it.

As soon, as the target was selected “ wifite ” ran the packet capture for “IP on Firewall”, it found the hosts connected to it and sent out de-auth packets for a few moments till the time the device was disconnected. Once the device got disconnected, the device tried to connect back to the WiFi router and during this process “ wifite ” captured the packet with the password for the WiFi in encrypted form.
Now, that once the capture file was present with me. I ran it against the rockyou.txt wordlist file using aircrack-ng, the command was as follows.
aircrack-ng -w rockyou.txt -b <bssid> <capture file name>
I let it run for a few minutes at max, when I got a hit on the password.

Once, I obtained the password, the next thing was to go ahead and sniff-out their traffic and look for interesting things.
Sniffing the packets
I was feeling ecstatic as soon as I figured out the password of IP on Firewall. The reason was, if they had not used such a simple password which was present in the rockyou.txt file, then the whole process would have been bogged down, I guess it was my lucky day.
Once I got into the network then I started ettercap, ( one of the best tool out there to sniff packets ). I wanted to capture each and every packet on their network, so I opened up terminal and typed in the following command.
ettercap -T -M arp -i eth0 /// -w test.cap
As soon as I initiated the ettercap, tons and tons of traffic was passing through on my terminal screen. I saved it all to the test.cap so that I can later on go through each and every packet on my device using Wireshark for detailed inspection.
If you want to go through the traffic on your Kali machine then you can use the following commands
cat test.cap | grep -a <keyword>
Using the above command you can search for the keyword you want to search for, the below command gave me the following output
cat test.cap | grep -a password

Once, I transferred the file to my laptop for further inspection I picked up many other login credentials which were entered on HTTP websites. The websites the users were visiting and many other interesting information.

So, now you know why there is such a high about intercepting other people’s traffic.
Tags
Hacking


Indian Nub LOL
ReplyDelete+
Delete